HawkSight Methodology
To carry out any security risk assessment in line with internationally accepted risk guidelines, you must answer three questions:
- What are you protecting?
- What are you protecting it from?
- How vulnerable is it?


Asset library
Your asset library is your prioritised register of all the assets you are protecting. It will be tailored for your purposes and is easy to update.
Assets include: People, Physical Assets, Information, ICT and Processes.
Your register will list all assets in order of importance or criticality.
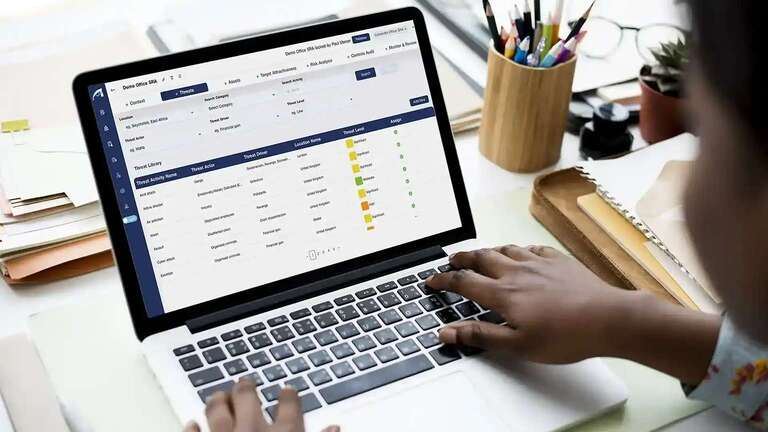
Threat library
What are you protecting it from?
Your security threat library contains a geo-located list of:
- Activities e.g. Theft
- Actors e.g. Criminals
- Drivers e.g. Financial gain
- Intent e.g. Determined
- Capability e.g. Moderate
- Threat level e.g. High
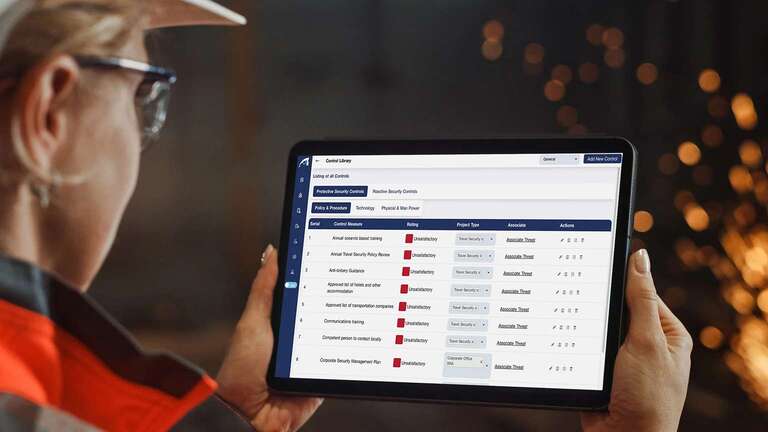
Control library
How vulnerable is it?
Carrying out a security control audit is essential to understand the vulnerability of your critical assets to the threats they may be exposed to.
Your security control library is a register of protective and reactive security controls linked to the risks they mitigate.
The security control audit allows you to assess the effectiveness of each security control, and then HawkSight re-evaluates the risk level in real time using our proprietary algorithm.
How does HawkSight work?
Our proprietary algorithm automates security risk assessments
The HawkSight algorithm calculates risk profile using external data sources and user-entered data. GIS technology enables the analysis and visualisation of risk through a tailored dashboard and report builder.

